Access Control Lists (ACLs) are a fundamental component of network security. It helps us control traffic flow within a network based on defined rules.
ACLs are categorized into two types: standard ACLs and extended ACLs. Standard ACL is further divided into standard-named ACL and standard-numbered ACL, while extended ACL is further divided into extended-named ACL and extended-numbered ACL.
In our previous article, we explored the standard named ACL configuration. In this blog post, we will focus on the standard numbered ACL configuration.
This is a video demonstration of what we will be covering in this article.
Network Topology
For this demonstration, we will use the same network topology as in our previous article. This setup consists of two routers, each connected to a switch. Additionally, two PCs are connected to each of the switches attached to the routers.

Below are the IP addresses used in this demonstration;
| Device | Default Gateway | Interface (Ip address) | Interface (Ip address) | Subnet Mask |
|---|---|---|---|---|
| Router 1(R1) | __ | G0/0/1 (192.168.1.1) | G0/0/0 (192.168.2.1) | 255.255.255.0 |
| Router 2(R2) | __ | G0/0/1 (192.168.3.1) | G0/0/0 (192.168.2.2) | 255.255.255.0 |
| PC0 | 192.168.3.1 | fa/0 (192.168.3.2) | __ | 255.255.255.0 |
| PC1 | 192.168.3.1 | fa/0 (192.168.3.3) | __ | 255.255.255.0 |
| PC2 | 192.168.1.1 | fa/0 (192.168.1.2) | __ | 255.255.255.0 |
| PC3 | 192.168.1.1 | fa/0 (192.168.1.3) | __ | 255.255.255.0 |
We maintained the network configuration according to the IP addresses shown in the table above. Also, we have completed the static route configuration to ensure that all PCs can communicate with each other.
Standard Numbered ACL Configuration
Now that we have set up interface IP addresses and static routing, we can proceed to implement the standard numbered ACL configurations on the network.
Configuration Objectives:
Our primary objectives for this configuration are as follows:
- Configure a standard numbered ACL on Router 1 (R1) to deny traffic from PC0 (192.168.3.2) to the network (192.168.1.0/24) while permitting all other traffic.
- Configure a standard numbered ACL on Router 2 (R2) to deny traffic from PC2 to the network (192.168.3.0/24) while permitting all other traffic.
Configuration Steps:
To achieve the objectives we outlined above using standard-numbered ACLs, the following configuration steps are needed:
Step 1: Configure a Standard Numbered ACL on Router 1 (R1)
R1(config)# access-list 10 deny host 192.168.3.2
R1(config)# access-list 10 permit anyIn the above ACL configuration:
- The first line creates a standard numbered ACL with the identifier 10.
- The second line denies traffic from host 192.168.3.2.
- The third line permits all other IP traffic.
Step 2: Apply the ACL to the interface on Router 1 (R1).
R1(config)# interface GigabitEthernet0/0/1
R1(config-if)# ip access-group 10 out
R1(config-if)# do writeThis configuration applies the ACL to traffic leaving the interface (GigabitEthernet0/0/1).
Step 3: Configure the Standard Numbered ACL on Router 2 (R2).
R2(config)# access-list 20 deny host 192.168.1.2
R2(config)# access-list 20 permit any
R2(config)# interface GigabitEthernet0/0/1
R2(config-if)# ip access-group 20 out
R2(config-if)# do write
In the above ACL configuration:
- The first line creates a standard numbered ACL with the identifier 20.
- The second line denies traffic from host 192.168.1.2.
- The third line permits all other IP traffic.
- The fourth line enters the interface (GigabitEthernet0/0/1).
- The fifth line applies the ACL rules to the interface.
Step 4: Test the Configuration
To validate that we have achieved our standard numbered ACL configuration objectives, I pinged from PC0 and PC1 to each of PC2 and PC3, and the pings from PC1 succeeded while the pings from PC0 failed. This shows that we have achieved our first objective.
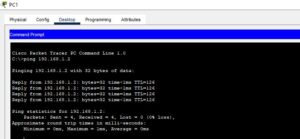
Also, I pinged from PC2 and PC3 to the two hosts on the network, 92.168.3.0/24, and all the pings failed. This shows that we have achieved our second objective.


I am a passionate Networking Associate specializing in Telecommunications.
With a degree in Electronic engineering, I possess a strong understanding of electronic systems and the intricacies of telecommunications networks. I gained practical experience and valuable insights working for a prominent telecommunications company.
Additionally, I hold certifications in networking, which have solidified my expertise in network architecture, protocols, and optimization.
Through my writing skills, I aim to provide accurate and valuable knowledge in the networking field.
Connect with me on social media using the links below for more insights.
You can contact me using [email protected] or connect with me using any of the social media account linked below


